Demystifying Internet Of Things Security: Unraveling the Complexities of Connected Devices

Welcome to the burgeoning realm of the Internet of Things (IoT),where everyday objects seamlessly intertwine with the digital world. From smart homes to industrial automation, IoT devices are revolutionizing our lives and transforming industries. However, this interconnected landscape also presents unique security challenges that demand our attention.
'Demystifying Internet Of Things Security' serves as your ultimate guide to understanding and mitigating IoT security risks. This comprehensive book empowers you with the knowledge to protect your connected devices, safeguard your data, and confidently navigate the ever-evolving digital landscape.
4.5 out of 5
| Language | : | English |
| File size | : | 42547 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 516 pages |
Chapter 1: Understanding the IoT Security Landscape
In this chapter, we lay the foundation for understanding IoT security by exploring the unique characteristics of connected devices and the potential threats they face. We examine common security risks, including unauthorized access, data breaches, and malware attacks, and discuss the vulnerabilities that make IoT devices susceptible to these threats.
Chapter 2: Implementing IoT Security Best Practices
Building upon the knowledge gained in Chapter 1, this chapter provides practical guidance on implementing effective IoT security measures. We cover essential best practices, such as strong password management, secure network configuration, and software updates. Additionally, we explore emerging technologies like blockchain and artificial intelligence (AI) that enhance IoT security.
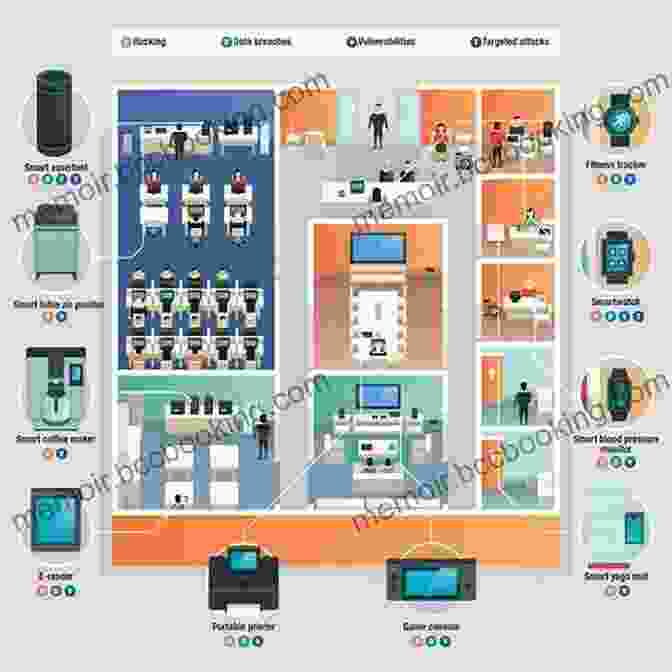
Chapter 3: Securing Smart Homes and Consumer IoT Devices
The proliferation of smart home devices has introduced a new frontier of security concerns. In this chapter, we focus on securing smart homes, covering topics such as Wi-Fi security, smart device vulnerabilities, and data privacy considerations. We provide practical tips and strategies to protect your home network and connected devices from unauthorized access and cyberattacks.
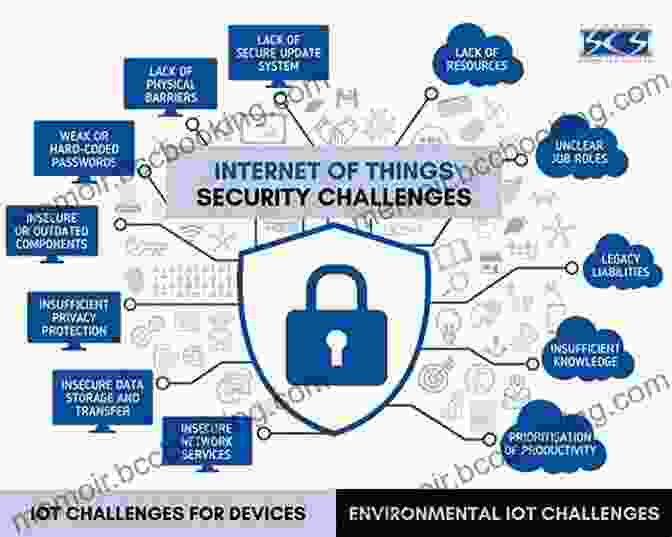
Chapter 4: IoT Security in Industrial Automation
IoT is also transforming industrial automation, introducing new risks and challenges. This chapter delves into the specific security considerations for industrial IoT (IIoT) systems, including vulnerabilities in operational technology (OT) networks, data integrity, and the potential for physical damage. We explore industry best practices and regulations to ensure the safety and security of IIoT deployments.
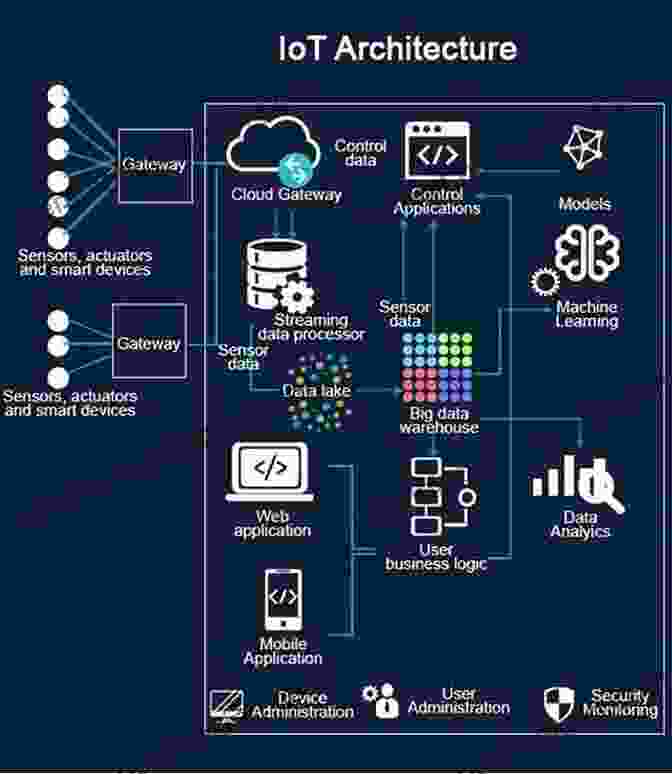
Chapter 5: Emerging IoT Security Trends and Technologies
The IoT security landscape is continuously evolving. In this chapter, we explore emerging trends and technologies that are shaping the future of IoT security. We discuss the role of AI in threat detection, the convergence of IoT and cloud computing, and the implications of quantum computing on IoT security. By understanding these trends, you can stay ahead of the curve and ensure your IoT deployments remain secure.
'Demystifying Internet Of Things Security' is your indispensable guide to understanding and mitigating IoT security risks. Whether you're a homeowner, business owner, or security professional, this book provides you with the knowledge and tools you need to protect your connected devices and data in the ever-expanding digital landscape.
Free Download your copy today and embark on a journey to demystify IoT security!
Free Download Now
4.5 out of 5
| Language | : | English |
| File size | : | 42547 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 516 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Barbara Belyea
Barbara Belyea Averell Ace Smith
Averell Ace Smith Annalisa Conti
Annalisa Conti B P Saville
B P Saville Asian Development Bank
Asian Development Bank Azar Nafisi
Azar Nafisi Antonio Nieto Rodriguez
Antonio Nieto Rodriguez Barbara Bick
Barbara Bick Anne Heltzel
Anne Heltzel Annette Thau
Annette Thau Annet Schaap
Annet Schaap Ann Zaprazny
Ann Zaprazny Audrey Wood
Audrey Wood B Jack Copeland
B Jack Copeland Aubrey Davis
Aubrey Davis Ana Ruiz
Ana Ruiz Ash Costello
Ash Costello Anthonissa Moger
Anthonissa Moger Archie Brain
Archie Brain Anna Costaras
Anna Costaras
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Kazuo IshiguroSpecial Relativity and Classical Field Theory: Unveiling the Mysteries of...
Kazuo IshiguroSpecial Relativity and Classical Field Theory: Unveiling the Mysteries of...
 John Dos PassosRediscovering the Joy and Wonder of Local, Sustainable Eating: Revisiting...
John Dos PassosRediscovering the Joy and Wonder of Local, Sustainable Eating: Revisiting...
 Edward ReedDeclutter and Conquer: The Ultimate Guide to Organizing Paperwork in the 21st...
Edward ReedDeclutter and Conquer: The Ultimate Guide to Organizing Paperwork in the 21st... George OrwellFollow ·13.9k
George OrwellFollow ·13.9k Nathaniel PowellFollow ·14.7k
Nathaniel PowellFollow ·14.7k Jeffery BellFollow ·13.7k
Jeffery BellFollow ·13.7k Aleksandr PushkinFollow ·4.5k
Aleksandr PushkinFollow ·4.5k Cormac McCarthyFollow ·7.7k
Cormac McCarthyFollow ·7.7k Paul ReedFollow ·16.1k
Paul ReedFollow ·16.1k Chase SimmonsFollow ·7.9k
Chase SimmonsFollow ·7.9k Jedidiah HayesFollow ·3.3k
Jedidiah HayesFollow ·3.3k

 Brayden Reed
Brayden ReedTeach Your Child They Have No Self Worth And They Will...
By Dr. Jane Doe ...

 Shawn Reed
Shawn ReedUnveiling Centuries of Tradition: History of Childbirth...
Journey into the heart of the...

 Brady Mitchell
Brady MitchellProven Guidelines For Healthy Multiple Pregnancy
Congratulations on your...

 Dylan Mitchell
Dylan MitchellHarness the Power of Sleep for Optimal Health and...
In the fast-paced,...

 Herman Melville
Herman MelvilleAlexander Hamilton: The Revolutionary Who Shaped...
Alexander Hamilton was a...
4.5 out of 5
| Language | : | English |
| File size | : | 42547 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 516 pages |